
Data Security Posture Management (DSPM)
Data Security Posture Management (DSPM) is a modern approach to identifying, monitoring, and securing sensitive data across cloud, SaaS, and data platforms. Unlike legacy tools, DSPM focuses on the data itself—where it resides, who has access, how it is being used, and whether it complies with privacy and security policies. By doing so, organizations can reduce risk, prove compliance, and protect business-critical assets. GoTrust DSPM provides continuous data security posture management solutions that automatically discover sensitive information, classify it, and remediate exposures with audit-ready evidence.



Data Security Posture Management (DSPM)
Data Security Posture Management (DSPM) is a modern approach to identifying, monitoring, and securing sensitive data across cloud, SaaS, and data platforms. Unlike legacy tools, DSPM focuses on the data itself—where it resides, who has access, how it is being used, and whether it complies with privacy and security policies. By doing so, organizations can reduce risk, prove compliance, and protect business-critical assets. GoTrust DSPM provides continuous data security posture management solutions that automatically discover sensitive information, classify it, and remediate exposures with audit-ready evidence.

Why Data Security Posture Management Matters ?
Why Data Security Posture Management Matters ?
Why Data Security Posture Management Matters ?
Data is now distributed across hybrid cloud, SaaS, and on-prem systems. Without visibility, organizations risk compliance violations, insider threats, and data leaks.
What is data security posture management?
It’s the discipline that ensures organizations know where their sensitive data lives, how it flows, and how to enforce the right controls—without slowing down business. GoTrust addresses this challenge by unifying data visibility, compliance enforcement, and automated remediation in one platform.
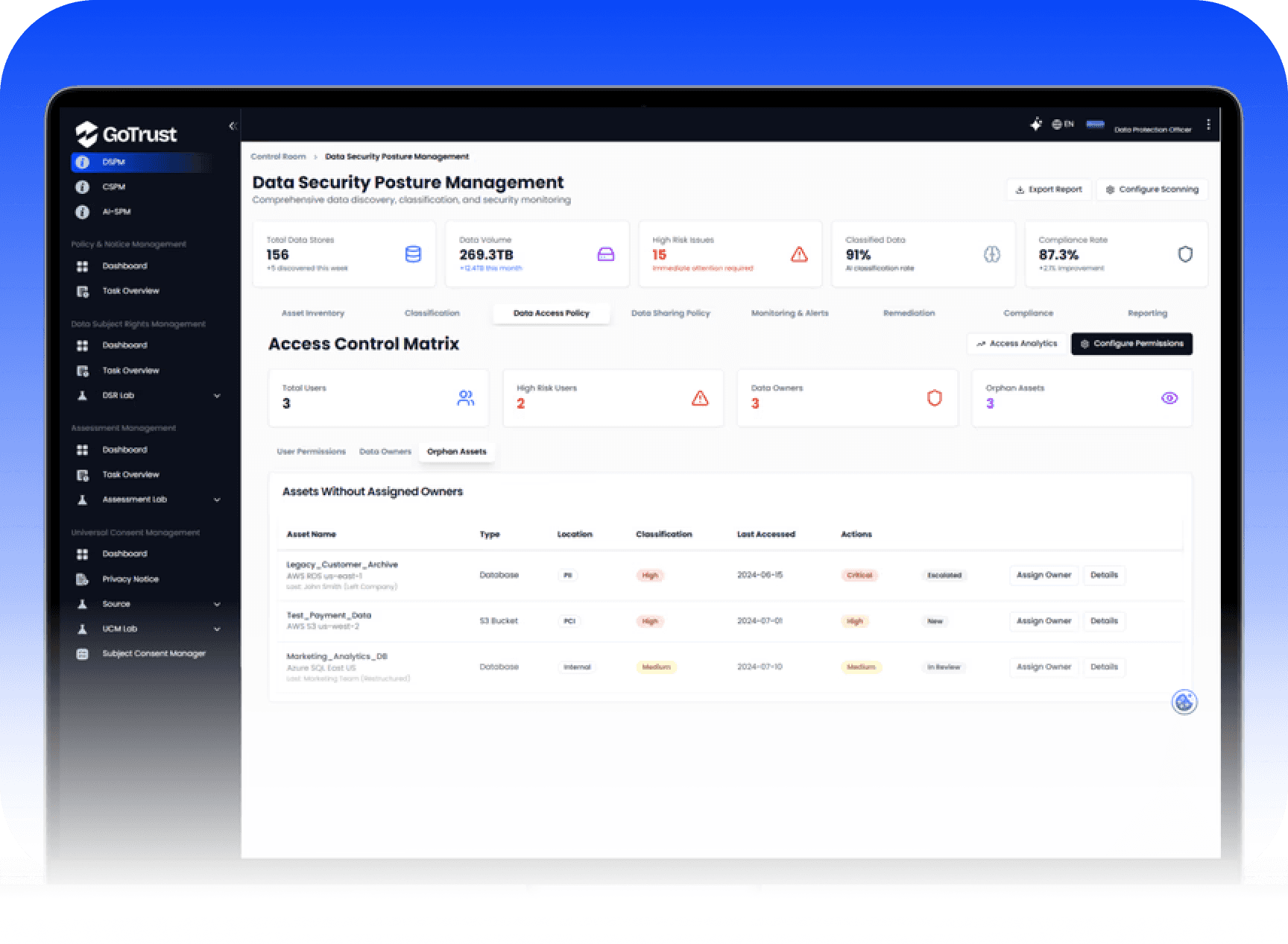



Data Governance & DSPM Platform:
Secure, Discover, and Control Your Data
Data Governance & DSPM Platform:
Secure, Discover, and Control Your Data
Take command of your entire data landscape with our unified platform. Ensure compliance, mitigate risks, and empower your organization through unparalleled data visibility and control.
01
Asset Discovery & Ingestion: Unifying Your Data Landscape
Everything You Need, In One Place
Asset Discovery & Ingestion: Unifying Your Data Landscape
Everything You Need, In One Place
Instantly connect to all your data sources, regardless of where they reside, to create a holistic view of your data estate.
Seamless Data Source Connection
Seamless Data Source Connection
Seamless Data Source Connection
Manual Connections: Easily connect to on-premises and private data sources, including Postgres, MySQL, Oracle, SFTP, and 300 more.
Manual Connections: Easily connect to on-premises and private data sources, including Postgres, MySQL, Oracle, SFTP, and 300 more.
Manual Connections: Easily connect to on-premises and private data sources, including Postgres, MySQL, Oracle, SFTP, and 300 more.
Cloud Integrations: Native, secure connections to major cloud providers: AWS, GCP, and Azure.
Cloud Integrations: Native, secure connections to major cloud providers: AWS, GCP, and Azure.
Cloud Integrations: Native, secure connections to major cloud providers: AWS, GCP, and Azure.
Review Added Connectors: A centralized dashboard to Review Added Connectors, manage credentials, and ensure connection health.
Review Added Connectors: A centralized dashboard to Review Added Connectors, manage credentials, and ensure connection health.
Review Added Connectors: A centralized dashboard to Review Added Connectors, manage credentials, and ensure connection health.
Scheduled Ingestion: Define your data discovery strategy. Schedule ingestion for immediate or later execution to start a comprehensive Data Discovery scan.
Scheduled Ingestion: Define your data discovery strategy. Schedule ingestion for immediate or later execution to start a comprehensive Data Discovery scan.
Scheduled Ingestion: Define your data discovery strategy. Schedule ingestion for immediate or later execution to start a comprehensive Data Discovery scan.



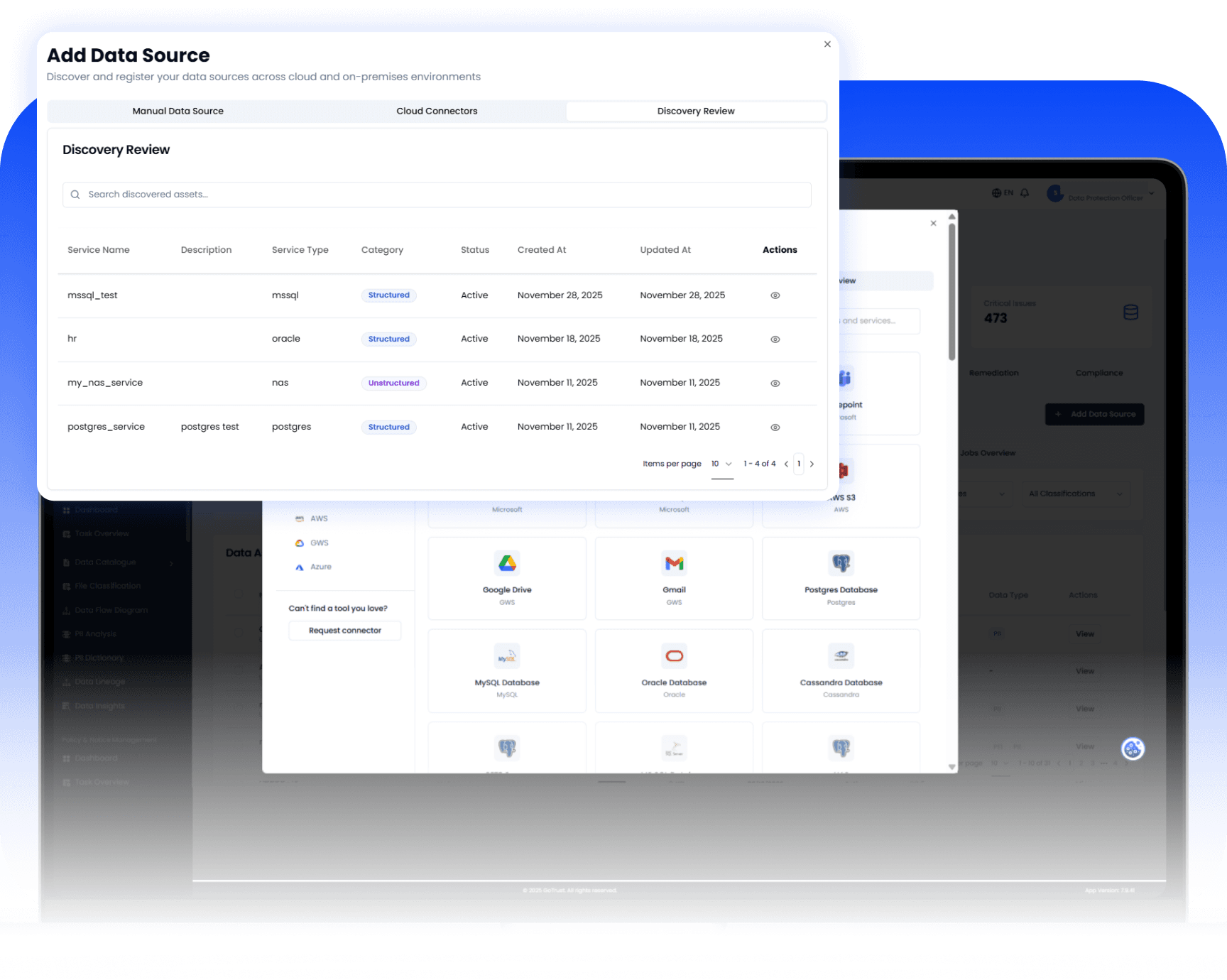



02
Data Discovery: Unified Data Assets View
Data Discovery: Unified Data Assets View
Data Discovery: Unified Data Assets View
From AI insights to auto-tracking — Spendex’s special features take your money management to the next level.
Asset Listing: A single, searchable list of all Data Assets with key information at a glance: size, type, Sensitive Data found, and access type.
Asset Status: Track the lifecycle and health of your data with statuses like Active, Inactive, and Stale Assets.
03
Metadata Management & Data Catalog: The Single Source of Truth
Build a rich, accurate Data Catalog by capturing, enriching, and curating metadata for every asset.
Core 1
Core 2
Comprehensive Metadata
View all critical information about your assets through detailed metadata tabs:
Overview & Business Metadata: Contextual information like description, business domain, and purpose.
Ownership Metadata: Details on Data Owner, Steward, and Custodian.
Organizational Metadata: Assign tags and assign department to assets.
Technical Metadata: Schema, data types, and sensitive information details.
Security and Compliance: Relevant security controls, tagged data policies and compliance tags.
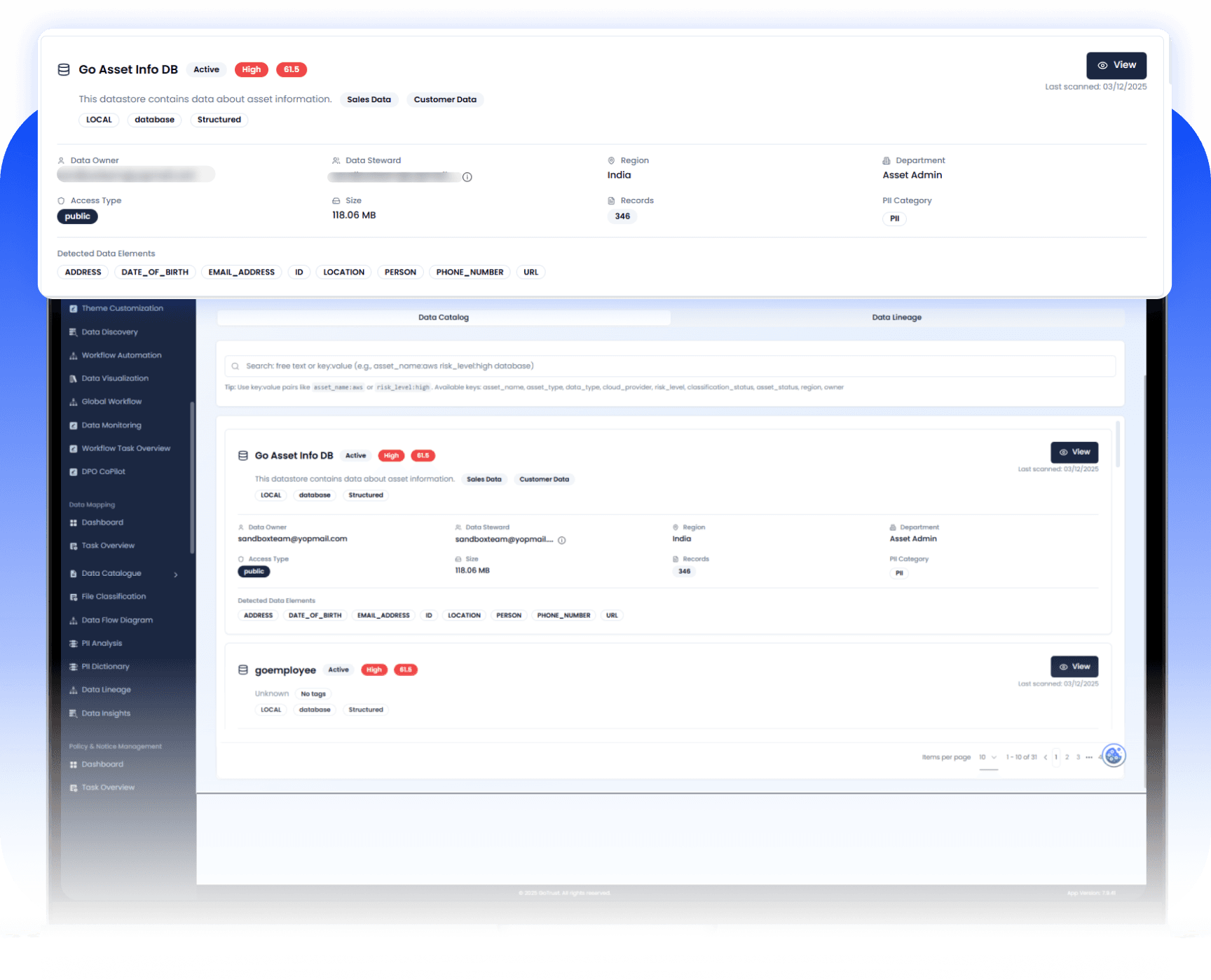

03
Metadata Management & Data Catalog: The Single Source of Truth
Build a rich, accurate Data Catalog by capturing, enriching, and curating metadata for every asset.
Core 1
Core 2
Comprehensive Metadata
View all critical information about your assets through detailed metadata tabs:
Overview & Business Metadata: Contextual information like description, business domain, and purpose.
Ownership Metadata: Details on Data Owner, Steward, and Custodian.
Organizational Metadata: Assign tags and assign department to assets.
Technical Metadata: Schema, data types, and sensitive information details.
Security and Compliance: Relevant security controls, tagged data policies and compliance tags.


03
Metadata Management & Data Catalog: The Single Source of Truth
Build a rich, accurate Data Catalog by capturing, enriching, and curating metadata for every asset.
Core 1
Core 2
Comprehensive Metadata
View all critical information about your assets through detailed metadata tabs:
Overview & Business Metadata: Contextual information like description, business domain, and purpose.
Ownership Metadata: Details on Data Owner, Steward, and Custodian.
Organizational Metadata: Assign tags and assign department to assets.
Technical Metadata: Schema, data types, and sensitive information details.
Security and Compliance: Relevant security controls, tagged data policies and compliance tags.


03
Metadata Management & Data Catalog: The Single Source of Truth
Build a rich, accurate Data Catalog by capturing, enriching, and curating metadata for every asset.
Core 1
Core 2
Comprehensive Metadata
View all critical information about your assets through detailed metadata tabs:
Overview & Business Metadata: Contextual information like description, business domain, and purpose.
Ownership Metadata: Details on Data Owner, Steward, and Custodian.
Organizational Metadata: Assign tags and assign department to assets.
Technical Metadata: Schema, data types, and sensitive information details.
Security and Compliance: Relevant security controls, tagged data policies and compliance tags.



04
Sensitive Data & PII Classification: Precision and Control
Automatically discover and classify sensitive data, allowing you to focus on the highest-risk assets.
Core 1
Core 2
Advanced PII Detection
Custom PII Dictionary: Add Custom PIIs in PII dictionary specific to your organization or industry.
Regex Definition: Define and add regex for custom PII detection, ensuring highly accurate and customized classification.
Unified Classification: View Classification unified data for all assets, providing a summary of all sensitive data found across your environment.

04
Sensitive Data & PII Classification: Precision and Control
Automatically discover and classify sensitive data, allowing you to focus on the highest-risk assets.
Core 1
Core 2
Advanced PII Detection
Custom PII Dictionary: Add Custom PIIs in PII dictionary specific to your organization or industry.
Regex Definition: Define and add regex for custom PII detection, ensuring highly accurate and customized classification.
Unified Classification: View Classification unified data for all assets, providing a summary of all sensitive data found across your environment.

04
Sensitive Data & PII Classification: Precision and Control
Automatically discover and classify sensitive data, allowing you to focus on the highest-risk assets.
Core 1
Core 2
Advanced PII Detection
Custom PII Dictionary: Add Custom PIIs in PII dictionary specific to your organization or industry.
Regex Definition: Define and add regex for custom PII detection, ensuring highly accurate and customized classification.
Unified Classification: View Classification unified data for all assets, providing a summary of all sensitive data found across your environment.

04
Sensitive Data & PII Classification: Precision and Control
Automatically discover and classify sensitive data, allowing you to focus on the highest-risk assets.
Core 1
Core 2
Advanced PII Detection
Custom PII Dictionary: Add Custom PIIs in PII dictionary specific to your organization or industry.
Regex Definition: Define and add regex for custom PII detection, ensuring highly accurate and customized classification.
Unified Classification: View Classification unified data for all assets, providing a summary of all sensitive data found across your environment.
05
Policy Enforcement & Risk Remediation: Proactive Security
Automate your governance policies to enforce security, access, and compliance rules in real-time.
Core 1
Core 2
Core 3
Policy Creation & Management
Risk Prioritization: Implement Risk-based Prioritization of assets by automatically scoring assets based on sensitivity, access, and compliance violations, ensuring you focus on the highest-risk data first.
Reduce Risk: Directly Reduce risk by remediation activities, tracking the quantifiable reduction in your risk score as policies are enforced and violations are resolved.
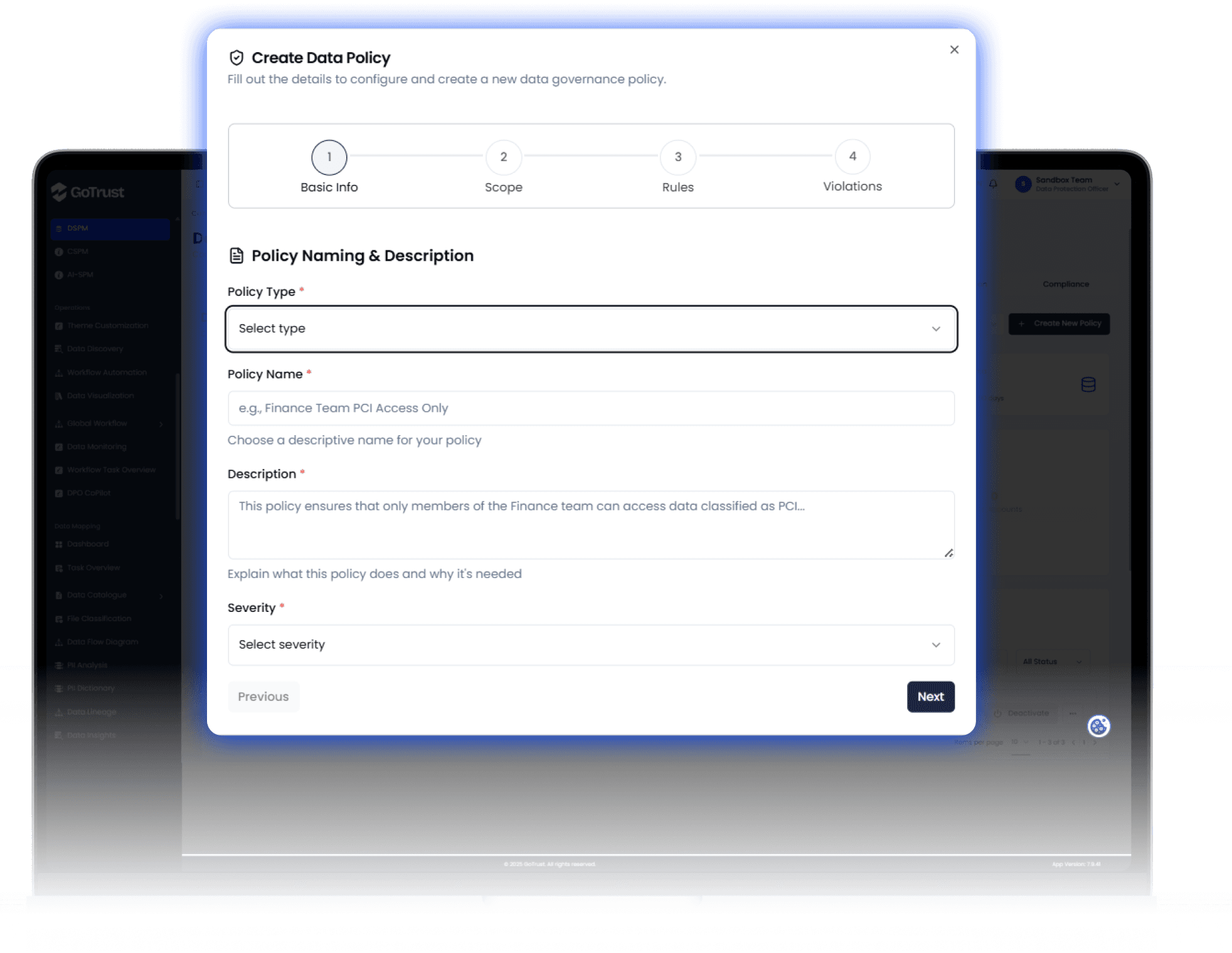
05
Policy Enforcement & Risk Remediation: Proactive Security
Automate your governance policies to enforce security, access, and compliance rules in real-time.
Core 1
Core 2
Core 3
Policy Creation & Management
Risk Prioritization: Implement Risk-based Prioritization of assets by automatically scoring assets based on sensitivity, access, and compliance violations, ensuring you focus on the highest-risk data first.
Reduce Risk: Directly Reduce risk by remediation activities, tracking the quantifiable reduction in your risk score as policies are enforced and violations are resolved.

05
Policy Enforcement & Risk Remediation: Proactive Security
Automate your governance policies to enforce security, access, and compliance rules in real-time.
Core 1
Core 2
Core 3
Policy Creation & Management
Risk Prioritization: Implement Risk-based Prioritization of assets by automatically scoring assets based on sensitivity, access, and compliance violations, ensuring you focus on the highest-risk data first.
Reduce Risk: Directly Reduce risk by remediation activities, tracking the quantifiable reduction in your risk score as policies are enforced and violations are resolved.

05
Policy Enforcement & Risk Remediation: Proactive Security
Automate your governance policies to enforce security, access, and compliance rules in real-time.
Core 1
Core 2
Core 3
Policy Creation & Management
Risk Prioritization: Implement Risk-based Prioritization of assets by automatically scoring assets based on sensitivity, access, and compliance violations, ensuring you focus on the highest-risk data first.
Reduce Risk: Directly Reduce risk by remediation activities, tracking the quantifiable reduction in your risk score as policies are enforced and violations are resolved.

Operationalization & Collaboration:
Integrating Governance into the Business
Move beyond mere detection. Operationalize data governance with cross-team workflows and seamless integration into your existing security and IT infrastructure.
Workflow & Collaboration
Cross-Team Collaboration: Facilitate Cross-team collaboration with shared dashboards, task assignment, and violation commenting for Data Owners, Security Teams, and IT Operations.
Automated Workflow Integration: Seamlessly integrate governance processes with your existing security tools via Automated workflow integrate with ITSM/SOAR tools like ServiceNow and Jira, enabling automatic ticket creation for violations, owner assignment, and status updates.
Testing & Deployment


Sandbox Environment: Utilize a Sandbox testing environment to safely simulate policy changes, test new PII definitions, and validate auto-remediation actions before deploying them to production.
Compliance & Reporting: Audit-Ready Evidence
Maintain continuous compliance by generating undeniable, audit-ready evidence for regulators and internal auditors.
Compliance Framework Mapping
Compliance Framework Mapping
Compliance Framework Mapping

Framework Listing
Get a clear Listing of Tagged Compliance Framework (e.g., GDPR, CCPA, HIPAA, DPDPA) per entity.

Framework Listing
Get a clear Listing of Tagged Compliance Framework (e.g., GDPR, CCPA, HIPAA, DPDPA) per entity.

Framework Listing
Get a clear Listing of Tagged Compliance Framework (e.g., GDPR, CCPA, HIPAA, DPDPA) per entity.

Framework Listing
Get a clear Listing of Tagged Compliance Framework (e.g., GDPR, CCPA, HIPAA, DPDPA) per entity.
Service Agreement Summary This agreement is made between NovaTech Solutions ("Provider") and Skybridge Enterprises ("Client") on March 15, 2025. The Provider agrees to deliver customized AI-driven data solutions, including predictive analytics and automated reporting, to the Client for a duration of 12 months. Key Terms:
Business Requirement View
View violation list per compliance business requirement wise, making audits and regulatory reporting straightforward.
Service Agreement Summary This agreement is made between NovaTech Solutions ("Provider") and Skybridge Enterprises ("Client") on March 15, 2025. The Provider agrees to deliver customized AI-driven data solutions, including predictive analytics and automated reporting, to the Client for a duration of 12 months. Key Terms:
Business Requirement View
View violation list per compliance business requirement wise, making audits and regulatory reporting straightforward.
Service Agreement Summary This agreement is made between NovaTech Solutions ("Provider") and Skybridge Enterprises ("Client") on March 15, 2025. The Provider agrees to deliver customized AI-driven data solutions, including predictive analytics and automated reporting, to the Client for a duration of 12 months. Key Terms:
Business Requirement View
View violation list per compliance business requirement wise, making audits and regulatory reporting straightforward.
Service Agreement Summary This agreement is made between NovaTech Solutions ("Provider") and Skybridge Enterprises ("Client") on March 15, 2025. The Provider agrees to deliver customized AI-driven data solutions, including predictive analytics and automated reporting, to the Client for a duration of 12 months. Key Terms:
Business Requirement View
View violation list per compliance business requirement wise, making audits and regulatory reporting straightforward.
Evidence Generation
Automatically generate Audit-ready evidence in policy, violation, and remediation logs, providing immutable proof of compliance activities and risk mitigation measures for every decision and action taken on the platform.
Evidence Generation
Automatically generate Audit-ready evidence in policy, violation, and remediation logs, providing immutable proof of compliance activities and risk mitigation measures for every decision and action taken on the platform.
Evidence Generation
Automatically generate Audit-ready evidence in policy, violation, and remediation logs, providing immutable proof of compliance activities and risk mitigation measures for every decision and action taken on the platform.
Evidence Generation
Automatically generate Audit-ready evidence in policy, violation, and remediation logs, providing immutable proof of compliance activities and risk mitigation measures for every decision and action taken on the platform.
Audit-Ready Evidence
Why GoTrust DSPM Data Security
Comprehensive Features to Secure Sensitive Data

Data-first approach
Protect sensitive data, not just infrastructure

Data-first approach
Protect sensitive data, not just infrastructure

Data-first approach
Protect sensitive data, not just infrastructure

Data-first approach
Protect sensitive data, not just infrastructure

Risk-based prioritization
Focus on the exposures that matter most

Risk-based prioritization
Focus on the exposures that matter most

Risk-based prioritization
Focus on the exposures that matter most

Risk-based prioritization
Focus on the exposures that matter most

Cross-team collaboration
Privacy, security, and data teams working together

Cross-team collaboration
Privacy, security, and data teams working together

Cross-team collaboration
Privacy, security, and data teams working together

Cross-team collaboration
Privacy, security, and data teams working together

Sandbox Testing Environment
Safe, isolated environment for testing governance policies and discovery workflows.

Sandbox Testing Environment
Safe, isolated environment for testing governance policies and discovery workflows.

Sandbox Testing Environment
Safe, isolated environment for testing governance policies and discovery workflows.

Sandbox Testing Environment
Safe, isolated environment for testing governance policies and discovery workflows.

Audit-ready evidence
Policies, violations, and remediation logs packaged for regulators

Audit-ready evidence
Policies, violations, and remediation logs packaged for regulators

Audit-ready evidence
Policies, violations, and remediation logs packaged for regulators

Audit-ready evidence
Policies, violations, and remediation logs packaged for regulators
GoTrust is not just another tool it is a DSPM data security posture management platform that empowers organizations to move beyond reactive security into proactive resilience.
Discover everything we’ve created with you in mind
Discover everything we’ve created with you in mind
From smart tools to seamless design features, every detail is crafted to make your experience smoother, faster, and more impactful.
From smart tools to seamless design features, every detail is crafted to make your experience smoother, faster, and more impactful.
Immediate visibility into data sprawl
Immediate visibility into data sprawl
Immediate visibility into data sprawl
Immediate visibility into data sprawl
Faster detection and remediation of risk
Faster detection and remediation of risk
Faster detection and remediation of risk
Faster detection and remediation of risk
Centralized governance across cloud and SaaS
Centralized governance across cloud and SaaS
Centralized governance across cloud and SaaS
Centralized governance across cloud and SaaS
Board-level reporting that translates security posture into business value
Board-level reporting that translates security posture into business value
Board-level reporting that translates security posture into business value
Board-level reporting that translates security posture into business value
Key Benefits
Business Value Through Security and Compliance



Stronger protection
Stronger protection
Stronger protection
Prevent data leaks with DSPM security and risk-based prioritization.
Prevent data leaks with DSPM security and risk-based prioritization.
Prevent data leaks with DSPM security and risk-based prioritization.
Faster compliance
Faster compliance
Faster compliance
Exportable evidence packs for GDPR, HIPAA, PCI DSS, ISO 27001, India DPDPA, and more.
Exportable evidence packs for GDPR, HIPAA, PCI DSS, ISO 27001, India DPDPA, and more.
Exportable evidence packs for GDPR, HIPAA, PCI DSS, ISO 27001, India DPDPA, and more.
Reduced risk
Reduced risk
Reduced risk
Rapidly shrink the attack surface by eliminating shadow and overexposed data.
Rapidly shrink the attack surface by eliminating shadow and overexposed data.
Rapidly shrink the attack surface by eliminating shadow and overexposed data.
Operational efficiency
Operational efficiency
Operational efficiency
Automated workflows integrate with ITSM/SOAR tools like ServiceNow and Jira.
Automated workflows integrate with ITSM/SOAR tools like ServiceNow and Jira.
Automated workflows integrate with ITSM/SOAR tools like ServiceNow and Jira.
Who Uses GoTrust DSPM
Who Uses GoTrust DSPM
Security leaders, IT teams, and compliance experts safeguarding sensitive data.
Security leaders, IT teams, and compliance experts safeguarding sensitive data.
CISOs & Security Leaders
Real-time posture, ROI, and board-ready reporting .
DPO & Privacy Teams
Compliance oversight with audit evidence.
Data & Cloud Teams
Right-sized access and clean data zones.
Application Owners
Guardrails without slowing down delivery .








GoTrust Knowledge Hub
Stay informed with insights, updates, and expert perspectives on data privacy, compliance, and digital trust.
Frequently Asked Questions (FAQ)
How is DSPM different from DLP or CSPM?
How is DSPM different from DLP or CSPM?
How is DSPM different from DLP or CSPM?
How is DSPM different from DLP or CSPM?
Will it slow down user workflows?
Will it slow down user workflows?
Will it slow down user workflows?
Will it slow down user workflows?
Can we create custom policies?
Can we create custom policies?
Can we create custom policies?
Can we create custom policies?
How do you ensure accountability?
How do you ensure accountability?
How do you ensure accountability?
How do you ensure accountability?
What about scoping access?
What about scoping access?
What about scoping access?
What about scoping access?






Talk To Our Expert
Schedule a session with our team to see how GoTrust unifies consent, privacy automation, DSPM, and governance into one intelligent compliance platform.


India
303, Tower C, ATS Bouquet, Noida Sector 132, U.P.

UAE
DIFC Innovation Hub, Gate Avenue, Zone D, Co-working Space Level 1 Al Mustaqbal St, Dubai

Netherlands
Cuserpark Amsterdam, De Cuserstraat 91, 1081CN, Amsterdam, Netherlands


India
303, Tower C, ATS Bouquet, Noida Sector 132, U.P.

UAE
DIFC Innovation Hub, Gate Avenue, Zone D, Co-working Space Level 1 Al Mustaqbal St, Dubai

Netherlands
Cuserpark Amsterdam, De Cuserstraat 91, 1081CN, Amsterdam, Netherlands


India
303, Tower C, ATS Bouquet, Noida Sector 132, U.P.

UAE
DIFC Innovation Hub, Gate Avenue, Zone D, Co-working Space Level 1 Al Mustaqbal St, Dubai

Netherlands
Cuserpark Amsterdam, De Cuserstraat 91, 1081CN, Amsterdam, Netherlands

India
303, Tower C, ATS Bouquet, Noida Sector 132, U.P.

UAE
DIFC Innovation Hub, Gate Avenue, Zone D, Co-working Space Level 1 Al Mustaqbal St, Dubai

Netherlands
Cuserpark Amsterdam, De Cuserstraat 91, 1081CN, Amsterdam, Netherlands















